基于Kubernetes Gitlab CICD
原文:https://i4t.com/4373.htmlphp
在大多数状况,构建项目都会占用大量的系统资源,若是让gitlab自己来运行构建任务的话,显然Gitlab的性能会大幅度降低。gitlab ci最大的做用就是管理各个项目的构建状态,所以,运行构建任务这种浪费资源的事情交给一个独立的gitlab runner来作就会好不少,更重要的是gitlab runner能够安装到不一样的机器上,甚至是咱们本机,这样彻底就不会影响Gitlab自己了。html
从gitlab8.0开始,gitlab CI就已经集成在Gitlab中,咱们只须要在项目中添加一个.gitlab-ci.yaml文件,而后运行一个Runner,便可进行持续集成。node
什么是Runner?
Gitlab Runner是一个开源项目,用于运行您的做业并将结果发送给gitlab。它与Gitlab CI结合使用,gitlab ci是Gitlab随附的用于协调做用的开源持续集成服务。git
Gitlab Runner是用Go编写的,能够做为一个二进制文件运行,不须要特定于语言的要求
它皆在GNU/Linux,MacOS和Windows操做系统上运行。若是要使用Docker,Gitlab Runner须要最少Docker v1.13.0golang
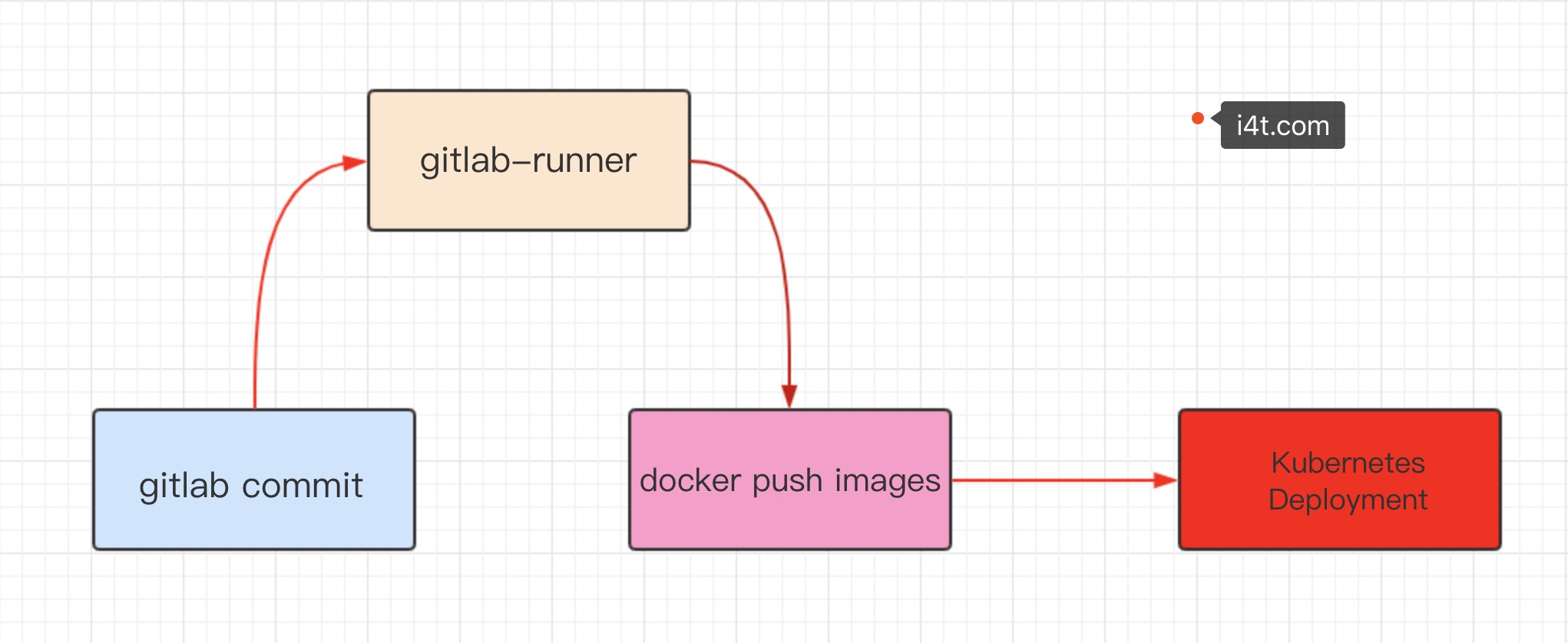
本文项目演示图redis
Gitlab 安装
gitlab官方提供了Helm的方式在Kubernetes集群中来快速安装,可是在使用的过程当中发现Helm提供的Chart包中有不少其余额外的配置,因此咱们这里自定义的方式来安装,也就是本身来自定义一些资源清单文件。sql
gitlab主要涉及3个应用:Redis、Postgresql、Gitlab核心程序docker
部署服务也能够在不跑在容器上,不影响gitlab的cicd。我这里使用k8s安装gitlab,而且没有使用持久化存储,若是想使用持久化存储能够在参考一下 prometheus搭建的文章
建立命名空间数据库
kubectl create namespace kube-ops
首先须要先部署Redis服务 (gitlab-redis.yaml)vim
apiVersion: apps/v1beta1
kind: Deployment
metadata:
name: redis
namespace: kube-ops
labels:
name: redis
spec:
template:
metadata:
name: redis
labels:
name: redis
spec:
containers:
- name: redis
image: sameersbn/redis
imagePullPolicy: IfNotPresent
ports:
- name: redis
containerPort: 6379
volumeMounts:
- mountPath: /var/lib/redis
name: data
livenessProbe:
exec:
command:
- redis-cli
- ping
initialDelaySeconds: 30
timeoutSeconds: 5
readinessProbe:
exec:
command:
- redis-cli
- ping
initialDelaySeconds: 5
timeoutSeconds: 1
volumes:
- name: data
emptyDir: {}
---
apiVersion: v1
kind: Service
metadata:
name: redis
namespace: kube-ops
labels:
name: redis
spec:
ports:
- name: redis
port: 6379
targetPort: redis
selector:
name: redis
数据库Postgresql部署 (gitlab-postgresql.yaml)
apiVersion: apps/v1beta1
kind: Deployment
metadata:
name: postgresql
namespace: kube-ops
labels:
name: postgresql
spec:
template:
metadata:
name: postgresql
labels:
name: postgresql
spec:
containers:
- name: postgresql
image: sameersbn/postgresql:10
imagePullPolicy: IfNotPresent
env:
- name: DB_USER
value: gitlab
- name: DB_PASS
value: passw0rd
- name: DB_NAME
value: gitlab_production
- name: DB_EXTENSION
value: pg_trgm
ports:
- name: postgres
containerPort: 5432
volumeMounts:
- mountPath: /var/lib/postgresql
name: data
livenessProbe:
exec:
command:
- pg_isready
- -h
- localhost
- -U
- postgres
initialDelaySeconds: 30
timeoutSeconds: 5
readinessProbe:
exec:
command:
- pg_isready
- -h
- localhost
- -U
- postgres
initialDelaySeconds: 5
timeoutSeconds: 1
volumes:
- name: data
emptyDir: {}
---
apiVersion: v1
kind: Service
metadata:
name: postgresql
namespace: kube-ops
labels:
name: postgresql
spec:
ports:
- name: postgres
port: 5432
targetPort: postgres
selector:
name: postgresql
gitlab应用配置以下 (gitlab.yaml)
这里没有使用官方的镜像仓库,而是使用第三方
http://www.damagehead.com/doc...
apiVersion: apps/v1beta1
kind: Deployment
metadata:
name: gitlab
namespace: kube-ops
labels:
name: gitlab
spec:
template:
metadata:
name: gitlab
labels:
name: gitlab
spec:
containers:
- name: gitlab
image: sameersbn/gitlab:11.8.1
imagePullPolicy: IfNotPresent
env:
- name: TZ
value: Asia/Shanghai
- name: GITLAB_TIMEZONE
value: Beijing
- name: GITLAB_SECRETS_DB_KEY_BASE
value: long-and-random-alpha-numeric-string
- name: GITLAB_SECRETS_SECRET_KEY_BASE
value: long-and-random-alpha-numeric-string
- name: GITLAB_SECRETS_OTP_KEY_BASE
value: long-and-random-alpha-numeric-string
- name: GITLAB_ROOT_PASSWORD
value: admin321
- name: GITLAB_ROOT_EMAIL
value: 381493251@qq.com
- name: GITLAB_HOST
value: 10.4.82.135:30004
- name: GITLAB_PORT
value: "80"
- name: GITLAB_SSH_PORT
value: "22"
- name: GITLAB_NOTIFY_ON_BROKEN_BUILDS
value: "true"
- name: GITLAB_NOTIFY_PUSHER
value: "false"
- name: GITLAB_BACKUP_SCHEDULE
value: daily
- name: GITLAB_BACKUP_TIME
value: 01:00
- name: DB_TYPE
value: postgres
- name: DB_HOST
value: postgresql
- name: DB_PORT
value: "5432"
- name: DB_USER
value: gitlab
- name: DB_PASS
value: passw0rd
- name: DB_NAME
value: gitlab_production
- name: REDIS_HOST
value: redis
- name: REDIS_PORT
value: "6379"
ports:
- name: http
containerPort: 80
- name: ssh
containerPort: 22
volumeMounts:
- mountPath: /home/git/data
name: data
livenessProbe:
httpGet:
path: /
port: 80
initialDelaySeconds: 180
timeoutSeconds: 5
readinessProbe:
httpGet:
path: /
port: 80
initialDelaySeconds: 5
timeoutSeconds: 1
volumes:
- name: data
emptyDir: {}
---
apiVersion: v1
kind: Service
metadata:
name: gitlab
namespace: kube-ops
labels:
name: gitlab
spec:
type: NodePort
ports:
- name: http
port: 80
targetPort: http
nodePort: 30004
- name: ssh
port: 22
targetPort: ssh
selector:
name: gitlab
################
GITLAB_HOST = 这里的域名是咱们Git clone代码的域名,我这里直接使用svc+port进行演示
接下来进行部署,须要提早建立好命名空间,上面咱们已经建立了
kubectl apply -f . deployment.apps/postgresql created service/postgresql created deployment.apps/redis created service/redis created deployment.apps/gitlab created service/gitlab created
检查pod和svc运行情况
[root@abcdocker gitlab]# kubectl get pod,svc -n kube-ops NAME READY STATUS RESTARTS AGE pod/gitlab-57cf47cd7d-cfpmn 0/1 Running 1 5m14s pod/postgresql-7c6bf8974d-r9djh 1/1 Running 0 5m19s pod/redis-c45ffd79b-75vbd 1/1 Running 0 5m17s NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE service/gitlab NodePort 10.254.212.182 <none> 80:30004/TCP,22:8530/TCP 5m11s service/postgresql ClusterIP 10.254.255.216 <none> 5432/TCP 5m18s service/redis ClusterIP 10.254.83.148 <none> 6379/TCP 5m15s
这里我采用的是nodePort的方式,而后咱们直接访问节点任意IP+30004端口便可访问 (若是pod没有报错,耐心等待一会就能够访问了)
用户名: root
密码:admin321
用户名和密码配置在gitlab配置文件中!
接下来建立个项目要进行演示
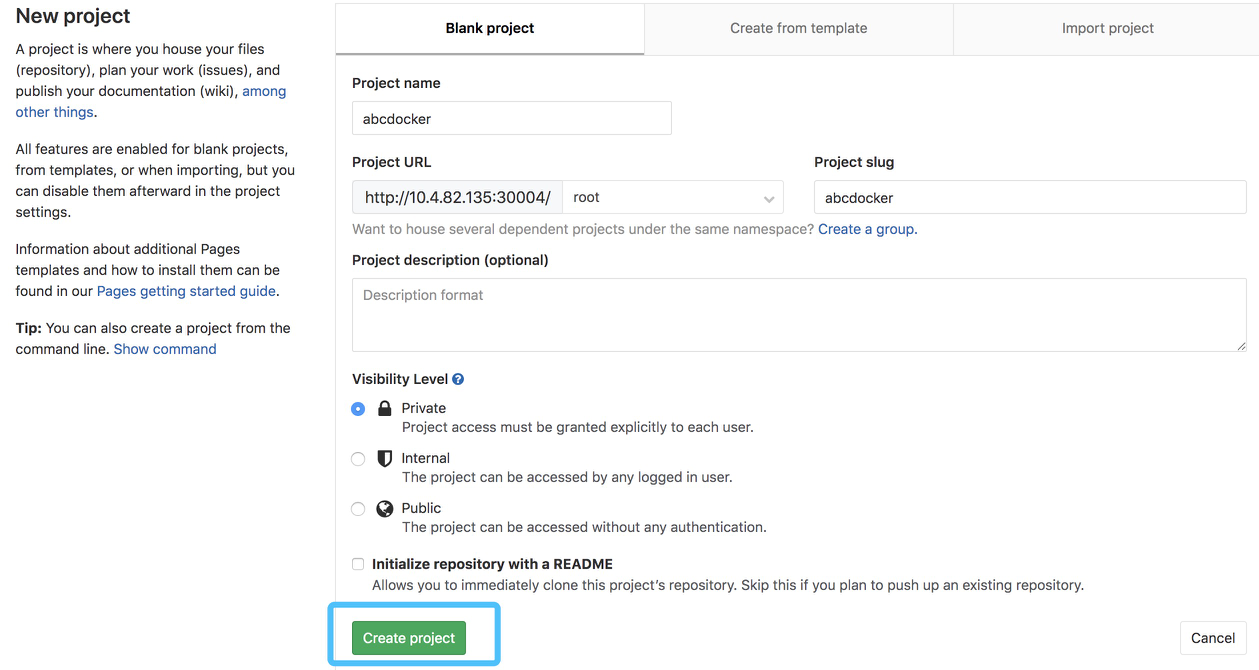
接下来添加提交代码
如何提交代码我这里就不详细介绍了,项目的REDME也提示咱们了
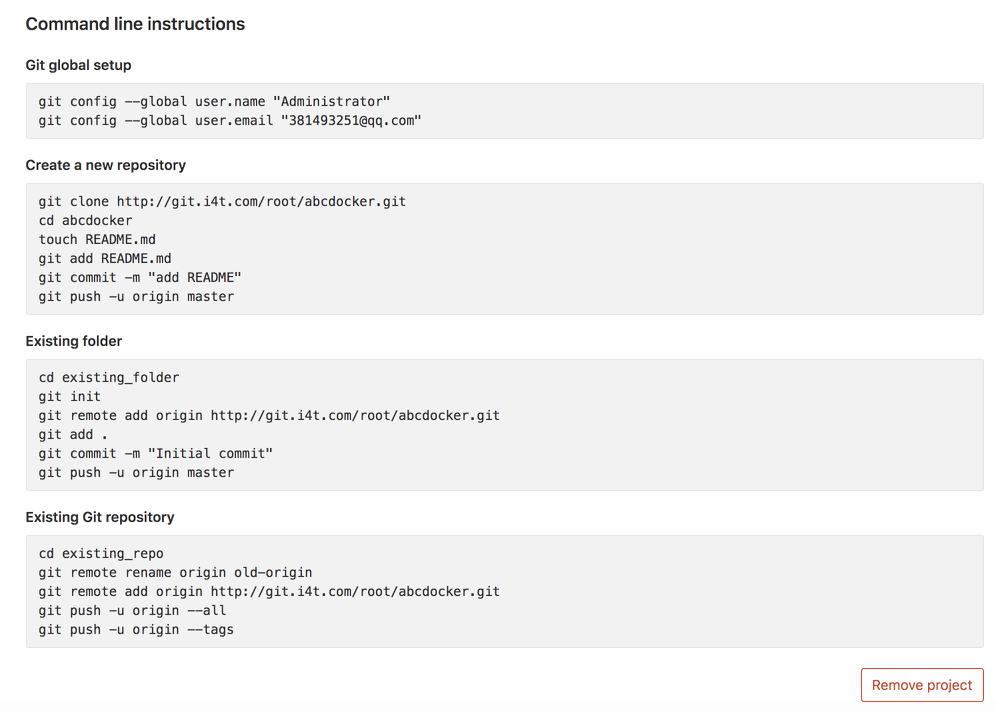
[root@abcdocker tmp]# git clone http://10.4.82.135:30004/root/abcdocker.git 正克隆到 'abcdocker'... Username for 'http://10.4.82.135:30004': root Password for 'http://root@10.4.82.135:30004': warning: 您彷佛克隆了一个空版本库。 wget http://down.i4t.com/abcdocker-gitlab-demo.tar.gz #git代码提交 git add * git add .* (记得提交隐藏文件) git commit -m "abcdocker" git push -u origin master
Gitlab Runner 安装
gitlab runner支持多种方式安装,我这里就采起在k8s中安装。
官方文档地址: https://docs.gitlab.com/runne...
首先咱们须要检查一下k8s集群的状态
[root@abcdocker ~]# kubectl cluster-info Kubernetes master is running at https://10.4.82.139:8443 CoreDNS is running at https://10.4.82.139:8443/api/v1/namespaces/kube-system/services/kube-dns:dns/proxy To further debug and diagnose cluster problems, use 'kubectl cluster-info dump'.
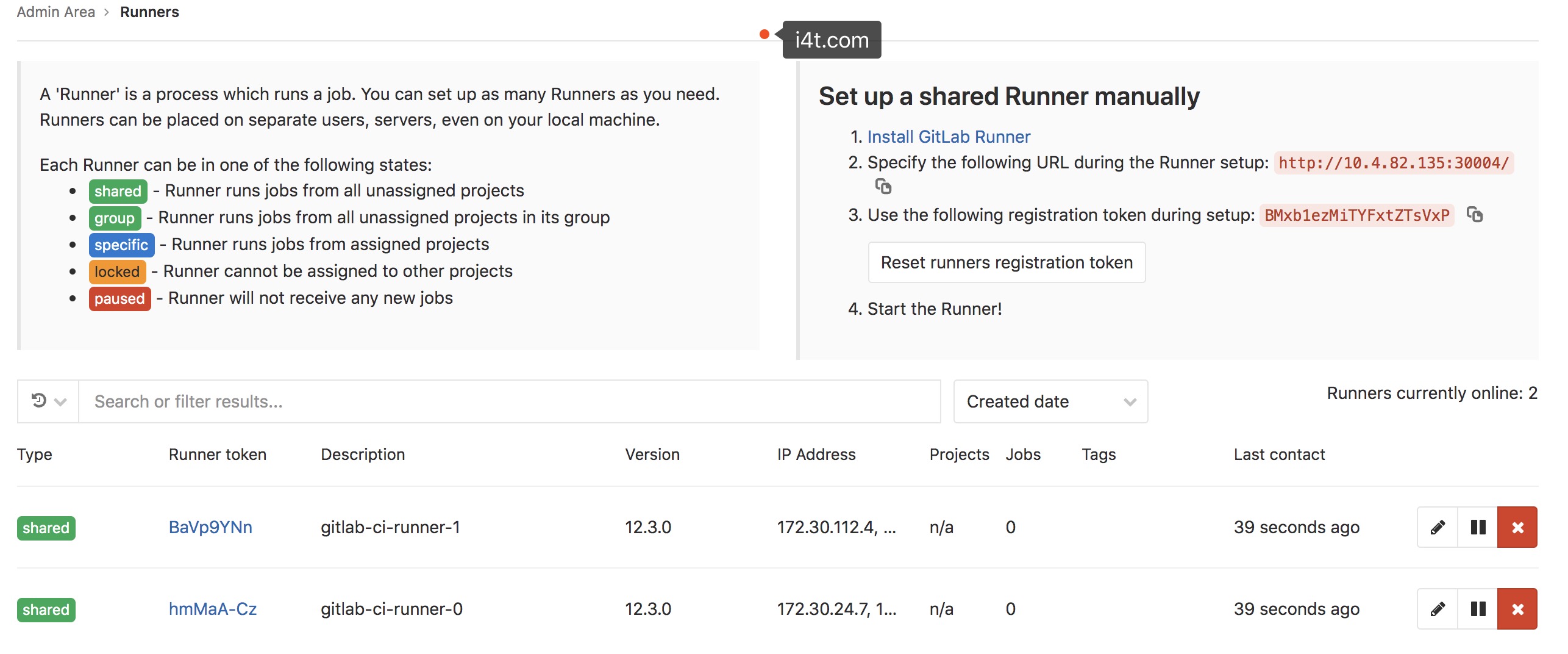
接下来咱们打开gitlab地址
以下图所示,左边表明runner状态,右边是配置runner信息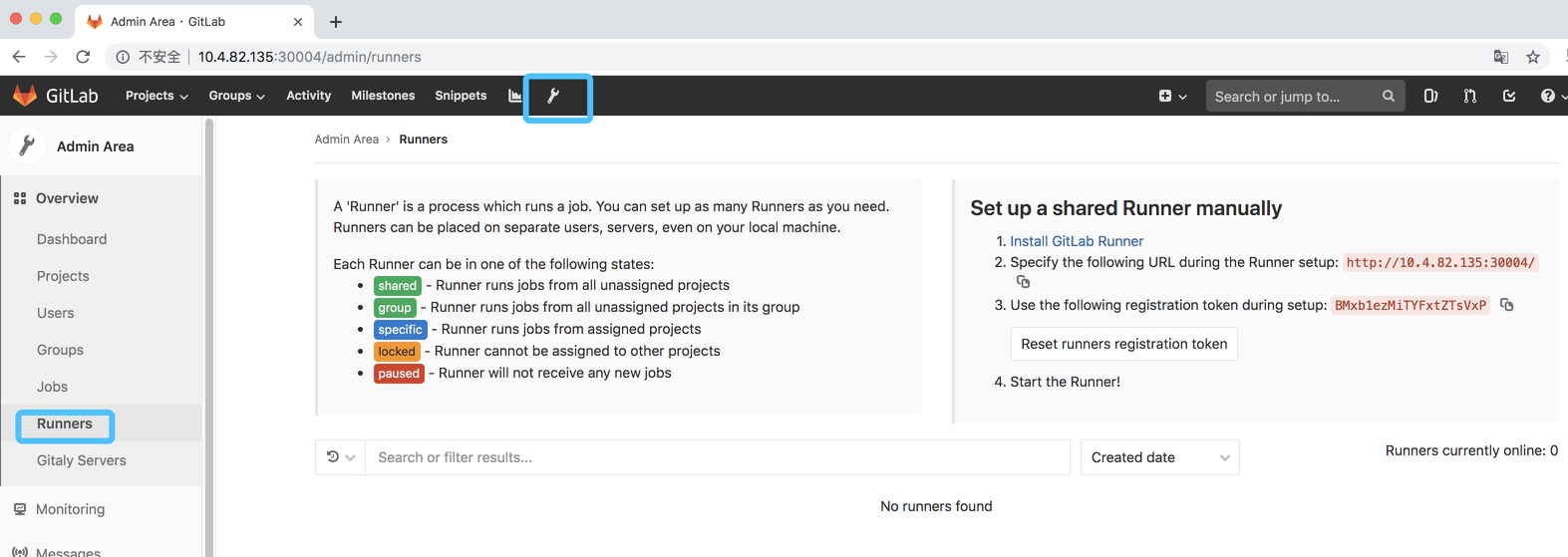
接下来进行配置gitlab runner资源清单 (runner-configmap.yaml)
apiVersion: v1
data:
REGISTER_NON_INTERACTIVE: "true"
REGISTER_LOCKED: "false"
METRICS_SERVER: "0.0.0.0:9100"
CI_SERVER_URL: "http://gitlab.kube-ops.svc.cluster.local/ci"
RUNNER_REQUEST_CONCURRENCY: "4"
RUNNER_EXECUTOR: "kubernetes"
KUBERNETES_NAMESPACE: "kube-ops"
KUBERNETES_PRIVILEGED: "true"
KUBERNETES_CPU_LIMIT: "1"
KUBERNETES_CPU_REQUEST: "500m"
KUBERNETES_MEMORY_LIMIT: "1Gi"
KUBERNETES_SERVICE_CPU_LIMIT: "1"
KUBERNETES_SERVICE_MEMORY_LIMIT: "1Gi"
KUBERNETES_HELPER_CPU_LIMIT: "500m"
KUBERNETES_HELPER_MEMORY_LIMIT: "100Mi"
KUBERNETES_PULL_POLICY: "if-not-present"
KUBERNETES_TERMINATIONGRACEPERIODSECONDS: "10"
KUBERNETES_POLL_INTERVAL: "5"
KUBERNETES_POLL_TIMEOUT: "360"
kind: ConfigMap
metadata:
labels:
app: gitlab-ci-runner
name: gitlab-ci-runner-cm
namespace: kube-ops
- CI_SERVER_URL 这个地址是gitlab的地址,若是gitlab在宿主机直接写宿主机的ip便可,容器是格式为svc名称.命名空间.svc.cluster.local (若是都按照个人文档来进行安装不须要修改别的配置了)
若是定义的gitlab域名并非经过外网DNS解析,而是经过/etc/hosts进行映射,那么咱们须要在Runner的Pod中去添加对应的hosts(我这里使用的是ip+端口)。咱们须要经过--pre-clone-script参数来指定一段脚原本添加hosts信息,也就是在ConfigMap中添加环境变量RUNNER_PRE_CLONE_SCRIPT的值
RUNNER_PRE_CLONE_SCRIPT = "echo 'xx.xx.xxx.xx git.i4t.com' >> /etc/hosts"
注意: 在ConfigMap添加新选项后,须要删除Gitlab ci Runner Pod
由于咱们使用envFrom来注入上面的这些环境变量而不是直接使用env(envfrom 经过将环境变量放置到ConfigMaps或Secrets来帮助减少清单文件)
若是咱们想添加其余选项,能够在Pod中运行gitlab-ci-multi-runner register --help 命令来查看全部可以使用的选项,只须要为配置的标志添加env变量便可
gitlab-runner@gitlab-ci-runner-0:/$ gitlab-ci-multi-runner register --help [...] --kubernetes-cpu-limit value The CPU allocation given to build containers (default: "1") [$KUBERNETES_CPU_LIMIT] --kubernetes-memory-limit value The amount of memory allocated to build containers (default: "4Gi") [$KUBERNETES_MEMORY_LIMIT] --kubernetes-service-cpu-limit value The CPU allocation given to build service containers (default: "1") [$KUBERNETES_SERVICE_CPU_LIMIT] --kubernetes-service-memory-limit value The amount of memory allocated to build service containers (default: "1Gi") [$KUBERNETES_SERVICE_MEMORY_LIMIT] --kubernetes-helper-cpu-limit value The CPU allocation given to build helper containers (default: "500m") [$KUBERNETES_HELPER_CPU_LIMIT] --kubernetes-helper-memory-limit value The amount of memory allocated to build helper containers (default: "3Gi") [$KUBERNETES_HELPER_MEMORY_LIMIT] --kubernetes-cpu-request value The CPU allocation requested for build containers [$KUBERNETES_CPU_REQUEST] ... --pre-clone-script value Runner-specific command script executed before code is pulled [$RUNNER_PRE_CLONE_SCRIPT] [...]
建立
[root@abcdocker gitlab]# kubectl apply -f runner-configmap.yaml configmap/gitlab-ci-runner-cm created [root@abcdocker gitlab]# kubectl get configmaps -n kube-ops NAME DATA AGE gitlab-ci-runner-cm 19 12s
咱们还须要配置一个用于注册、运行和取消gitlab ci runner的小脚本。只有当Pod正常经过Kubernetes (TERM信号)终止时,才会触发注销注册。若是强行终止Pod(SIGKILL信号),Runner将不会本身注销自身。必须手动完成对这种Runner的清理 (二进制安装非K8s上不受这个影响)
(runner-scripts-cm.yaml)
apiVersion: v1
data:
run.sh: |
#!/bin/bash
unregister() {
kill %1
echo "Unregistering runner ${RUNNER_NAME} ..."
/usr/bin/gitlab-ci-multi-runner unregister -t "$(/usr/bin/gitlab-ci-multi-runner list 2>&1 | tail -n1 | awk '{print $4}' | cut -d'=' -f2)" -n ${RUNNER_NAME}
exit $?
}
trap 'unregister' EXIT HUP INT QUIT PIPE TERM
echo "Registering runner ${RUNNER_NAME} ..."
/usr/bin/gitlab-ci-multi-runner register -r ${GITLAB_CI_TOKEN}
sed -i 's/^concurrent.*/concurrent = '"${RUNNER_REQUEST_CONCURRENCY}"'/' /home/gitlab-runner/.gitlab-runner/config.toml
echo "Starting runner ${RUNNER_NAME} ..."
/usr/bin/gitlab-ci-multi-runner run -n ${RUNNER_NAME} &
wait
kind: ConfigMap
metadata:
labels:
app: gitlab-ci-runner
name: gitlab-ci-runner-scripts
namespace: kube-ops
建立
[root@abcdocker gitlab]# kubectl apply -f runner-scripts-cm.yaml configmap/gitlab-ci-runner-scripts created
咱们须要建立一个GITLAB_CI_TOKEN,而后咱们使用gitlab ci runner token来建立一个Kubernetes secret对象。须要提早对token进行base64转码
[root@abcdocker gitlab]# echo BMxb1ezMiTYFxtZTsVxP|base64 -w0 Qk14YjFlek1pVFlGeHRaVHNWeFAK
这里的token就是咱们gitlab runner上截图的地方,base64只有在k8s环境上须要
以下图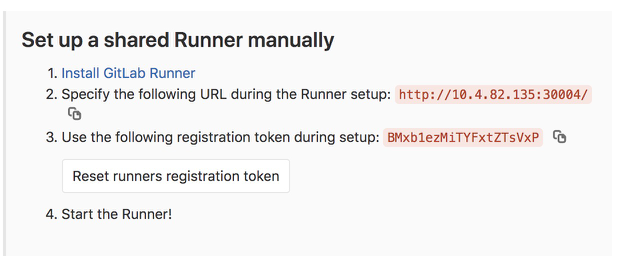
接下来使用上面的token建立一个Sercret对象 (gitlab-ci-token-secret.yaml)
[root@abcdocker gitlab]# cat gitlab-ci-token-secret.yaml
apiVersion: v1
kind: Secret
metadata:
name: gitlab-ci-token
namespace: kube-ops
labels:
app: gitlab-ci-runner
data:
GITLAB_CI_TOKEN: Qk14YjFlek1pVFlGeHRaVHNWeFAK
建立
[root@abcdocker gitlab]# kubectl apply -f gitlab-ci-token-secret.yaml secret/gitlab-ci-token created
接下来建立真正运行Runner的控制器镜像,这里使用Statefulset,在开始运行的时候,尝试取消注册全部的同名Runner,当节点丢失时(即NodeLost事件),这尤为有用,而后再尝试注册本身并开始运行。在正常中止Pod的时候,Runner将会运行unregister命令来尝试取消本身,因此gitlab就不能再使用这个Runner,这个则是经过kubernetes Pod生命周期中的hooks来完成的
runner-statefulset.yaml
apiVersion: apps/v1beta1
kind: StatefulSet
metadata:
name: gitlab-ci-runner
namespace: kube-ops
labels:
app: gitlab-ci-runner
spec:
updateStrategy:
type: RollingUpdate
replicas: 2
serviceName: gitlab-ci-runner
template:
metadata:
labels:
app: gitlab-ci-runner
spec:
volumes:
- name: gitlab-ci-runner-scripts
projected:
sources:
- configMap:
name: gitlab-ci-runner-scripts
items:
- key: run.sh
path: run.sh
mode: 0755
serviceAccountName: gitlab-ci
securityContext:
runAsNonRoot: true
runAsUser: 999
supplementalGroups: [999]
containers:
- image: gitlab/gitlab-runner:latest
name: gitlab-ci-runner
command:
- /scripts/run.sh
envFrom:
- configMapRef:
name: gitlab-ci-runner-cm
- secretRef:
name: gitlab-ci-token
env:
- name: RUNNER_NAME
valueFrom:
fieldRef:
fieldPath: metadata.name
ports:
- containerPort: 9100
name: http-metrics
protocol: TCP
volumeMounts:
- name: gitlab-ci-runner-scripts
mountPath: "/scripts"
readOnly: true
restartPolicy: Always
上面咱们命名了一个gitlab-ci的serviceAccount,这里要新建一个rbac文件 (runner-rbac.yaml)
apiVersion: v1
kind: ServiceAccount
metadata:
name: gitlab-ci
namespace: kube-ops
---
kind: Role
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: gitlab-ci
namespace: kube-ops
rules:
- apiGroups: [""]
resources: ["*"]
verbs: ["*"]
---
kind: RoleBinding
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: gitlab-ci
namespace: kube-ops
subjects:
- kind: ServiceAccount
name: gitlab-ci
namespace: kube-ops
roleRef:
kind: Role
name: gitlab-ci
apiGroup: rbac.authorization.k8s.io
建立完毕
[root@abcdocker gitlab]# kubectl apply -f runner-rbac.yaml serviceaccount/gitlab-ci created role.rbac.authorization.k8s.io/gitlab-ci created rolebinding.rbac.authorization.k8s.io/gitlab-ci created [root@abcdocker gitlab]# kubectl apply -f runner-statefulset.yaml statefulset.apps/gitlab-ci-runner created
接下来咱们检查咱们建立的
[root@abcdocker gitlab]# kubectl get pod,svc,cm -n kube-ops NAME READY STATUS RESTARTS AGE pod/gitlab-57cf47cd7d-cfpmn 1/1 Running 1 47h pod/gitlab-ci-runner-0 1/1 Running 0 2m51s pod/gitlab-ci-runner-1 1/1 Running 0 119s pod/postgresql-7c6bf8974d-r9djh 1/1 Running 0 47h pod/redis-c45ffd79b-75vbd 1/1 Running 0 47h NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE service/gitlab NodePort 10.254.212.182 <none> 80:30004/TCP,22:8530/TCP 47h service/postgresql ClusterIP 10.254.255.216 <none> 5432/TCP 47h service/redis ClusterIP 10.254.83.148 <none> 6379/TCP 47h NAME DATA AGE configmap/gitlab-ci-runner-cm 19 150m configmap/gitlab-ci-runner-scripts 1 78m #目前pod gitlab-ci-runner0和1都已经属于正常的运行状态
此时咱们查看gitlab中的Runners就已经将这2个pod节点添加进来了
这里咱们也能够更改Runner的一些配置,好比添加tag标签等
gitlab CICD 配置
首先咱们须要有一个项目,接下来咱们进行gitlab配置演示
#项目下载 wget http://down.i4t.com/gitlab-ci-k8s-demo.tar.gz #须要修改
须要各位本身进行配置gitlab,新建一个项目并上传。详细步骤这里再也不介绍
若是项目里面有勾选Auto DevOps记得取消,对咱们的cicd会有影响
项目介绍
本次环境使用的是go环境,只是为了演示。Java和php的构建方式也差很少相同。初次演示能够经过个人模板进行演示
这里其实是引用了相似于Jenkins pipline的脚本格式
gitlab-ci.yaml介绍
image:
name: golang:1.10.3-stretch #这里的全局镜像就是当下面的stage里面没有定义镜像时,使用的就是这里全局的镜像地址。可是当咱们指定镜像时,就不会使用全局变量
entrypoint: ["/bin/sh", "-c"]
# The problem is that to be able to use go get, one needs to put
# the repository in the $GOPATH. So for example if your gitlab domain
# is mydomainperso.com, and that your repository is repos/projectname, and
# the default GOPATH being /go, then you'd need to have your
# repository in /go/src/mydomainperso.com/repos/projectname
# Thus, making a symbolic link corrects this.
before_script: #在咱们的go环境中,默认的go path是在咱们go的目录下面,因此咱们要在go目录下面建立一个src。至关于咱们项目中的一个地址 。而后咱们将项目地址ln到咱们的go path地址中去
- mkdir -p "/go/src/git.qikqiak.com/${CI_PROJECT_NAMESPACE}"
- ln -sf "${CI_PROJECT_DIR}" "/go/src/git.i4t.com/${CI_PROJECT_PATH}"
- cd "/go/src/git.i4t.com/${CI_PROJECT_PATH}/"
stages: ##这里stages表明一个项目,每一个名称下面能够建立一个或多个任务,而且是同时执行的。前面是stages执行完毕后才会执行下一个
- test
- build
- release
- review
- deploy
test1:
stage: test #这里经过stage进行匹配任务标签,而且test1和test2是属于队形操做,并非串行操做
script:
- make test
test2:
stage: test
script:
- sleep 3
- echo "We did it! Something else runs in parallel!"
compile: #这build阶段执行一个compile任务
stage: build #当咱们上面test执行完毕后,就会开始执行build操做
script: #经过script执行一个具体的命令,这里是进行make build操做
# Add here all the dependencies, or use glide/govendor/...
# to get them automatically.
- make build #这里的build是在咱们build咱们Makefile里面的脚本,固然也能够修改其余成命令
artifacts: #这里的就是将咱们build的一个值挂载一下,能够到下面的job进行获取,咱们在浏览器上也能够获取到这个文件,能够直接下载。至关于将app这个标签的文件暴露出来
paths:
- app
image_build: #这里到了release阶段,作了一个imageBuild操做(这里指的就是镜像构建)这里使用docker build就须要docker命令
stage: release
image: docker:latest #这里的镜像就是使用docker的镜像,这个镜像是提供了一个docker命令,当咱们docker build的时候须要将全部的文件提交到一个docker daemon里面去作的一个构建工做。因此这里还须要一个service,来指定docker所依赖的服务。下面咱们就引用了一个docker in docker的一个镜像。这个service实际上就是咱们docker镜像所依赖的一个服务,若是咱们还依赖其余镜像,直接在下面添加就能够了
variables: #这里的配置主要是指定docker的一个host
DOCKER_DRIVER: overlay
DOCKER_HOST: tcp://localhost:2375
services: #这里就是表明咱们service暴露的端口就是2375,至关于将咱们docker的客户端和service关联起来了。这样当咱们执行docker build的命令就会调用咱们的docker daemon来进行一个build的操做
- name: docker:17.03-dind
command: ["--insecure-registry=registry.i4t.com"] #这里能够写私有仓库,可是为了演示,我这里直接修改成公有仓库,若是这里不写仓库地址会出现509的错误
script: #这里就是执行一个真正的脚本,来进行build一个操做
- docker info
- docker login -u "${CI_REGISTRY_USER}" -p "${CI_REGISTRY_PASSWORD}" registry.i4t.com #这里的用户名密码不方便写死,因此这里写成变量。在gitlab项目中进行添加配置
- docker build -t "${CI_REGISTRY_IMAGE}:latest" .
- docker tag "${CI_REGISTRY_IMAGE}:latest" "${CI_REGISTRY_IMAGE}:${CI_COMMIT_REF_NAME}" #须要说明一点,这里的ci_commit_ref_name实际上就是gitlab commit版本号,在以前的jenkins中已经使用过不少次,具体不详细介绍(须要请点击i4t.com找jenkins文档)
- test ! -z "${CI_COMMIT_TAG}" && docker push "${CI_REGISTRY_IMAGE}:latest"
- docker push "${CI_REGISTRY_IMAGE}:${CI_COMMIT_REF_NAME}"
deploy_review: #这里这一个预览环境,至关于开发环境。
image: registry.cn-beijing.aliyuncs.com/abcdocker/k8s:kubectl #这里的image是一个kubectl的命令,这个镜像实际上就是内置了一个二进制的kubectl命令,可是咱们知道若是咱们想使用kubectl命令是须要提供apiserver的一些相关配置,才能够链接到咱们的kubernetes集群
stage: review
only:
- branches #只有提交到咱们的gitlab指定的分支上,才会执行咱们的这个job任务。若是提交的是tag上来,是不会触发咱们的任务的
except:
- tags
environment: #这里咱们定义了一个环境,而且在里面定义了一个url。这样当咱们触发了review job,咱们能够经过下面的域名进行访问
name: dev
url: https://dev-gitlab-k8s-demo.i4t.com #这里的若是安装了Traefik能够直接绑定host或者经过dns进行配置,也能够是svc
on_stop: stop_review #这里咱们添加了一个回调,当咱们中止咱们dev环境时去作的一件事情(这里的stop_review在下面进行查看)
script: #这里的命令就是替换常常镜像版本号的一些操做,deployment等相关文件都须要提交的gitlab上
- kubectl version
- cd manifests/
- sed -i "s/__CI_ENVIRONMENT_SLUG__/${CI_ENVIRONMENT_SLUG}/" deployment.yaml ingress.yaml service.yaml
- sed -i "s/__VERSION__/${CI_COMMIT_REF_NAME}/" deployment.yaml ingress.yaml service.yaml
- |
if kubectl apply -f deployment.yaml | grep -q unchanged; then
echo "=> Patching deployment to force image update."
kubectl patch -f deployment.yaml -p "{\"spec\":{\"template\":{\"metadata\":{\"annotations\":{\"ci-last-updated\":\"$(date +'%s')\"}}}}}"
else
echo "=> Deployment apply has changed the object, no need to force image update."
fi
- kubectl apply -f service.yaml || true
- kubectl apply -f ingress.yaml
- kubectl rollout status -f deployment.yaml
- kubectl get all,ing -l ref=${CI_ENVIRONMENT_SLUG}
stop_review: #这里就是上面review中引用的stop_review。中止前作的一件事情
image: registry.cn-beijing.aliyuncs.com/abcdocker/k8s:kubectl
stage: review
variables:
GIT_STRATEGY: none
when: manual
only: #这里除了咱们的master分支和tag,其余的分支均可以进行一个branches job任务
- branches
except:
- master
- tags
environment:
name: dev #这里的环境也是dev
action: stop #执行的动做,这里表明执行stop动做
script: #这里执行的命令就是将以前构建的项目中的镜像及相关配置都进行删除的一个操做
- kubectl version
- kubectl delete ing -l ref=${CI_ENVIRONMENT_SLUG} #这里经过ref标签进行匹配删除(这里中的环境配置都是在咱们manifests目录中引用)
- kubectl delete all -l ref=${CI_ENVIRONMENT_SLUG}
deploy_live: #这里是真正的deploy阶段,真正去部署(这里是定义了一个deploy_live的任务)
image: registry.cn-beijing.aliyuncs.com/abcdocker/k8s:kubectl #这里仍是使用的kubectl命令
stage: deploy
environment: #这里定义了一个标签为live的一个线上环境
name: live
url: https://live-gitlab-k8s-demo.i4t.com #这里就是部署完成以后线上的一个地址
only:
- tags #只有咱们提交一个tag标签的时候,才会执行job任务
when: manual #这里的参数表明手动的进行执行
script: #下面的命令操做和前面的dev环境中配置的命令是同样的,实际上就是一个替换镜像的一个操做
- kubectl version
- cd manifests/
- sed -i "s/__CI_ENVIRONMENT_SLUG__/${CI_ENVIRONMENT_SLUG}/" deployment.yaml ingress.yaml service.yaml
- sed -i "s/__VERSION__/${CI_COMMIT_REF_NAME}/" deployment.yaml ingress.yaml service.yaml
- kubectl apply -f deployment.yaml
- kubectl apply -f service.yaml
- kubectl apply -f ingress.yaml
- kubectl rollout status -f deployment.yaml
- kubectl get all,ing -l ref=${CI_ENVIRONMENT_SLUG}
如今咱们要配置一下kubectl,默认状况下kubectl须要使用证书才能够链接到k8s集群。在服务器上默认使用的是/root/.kube/config,gitlab 也有添加证书的位置,咱们进行添加配置
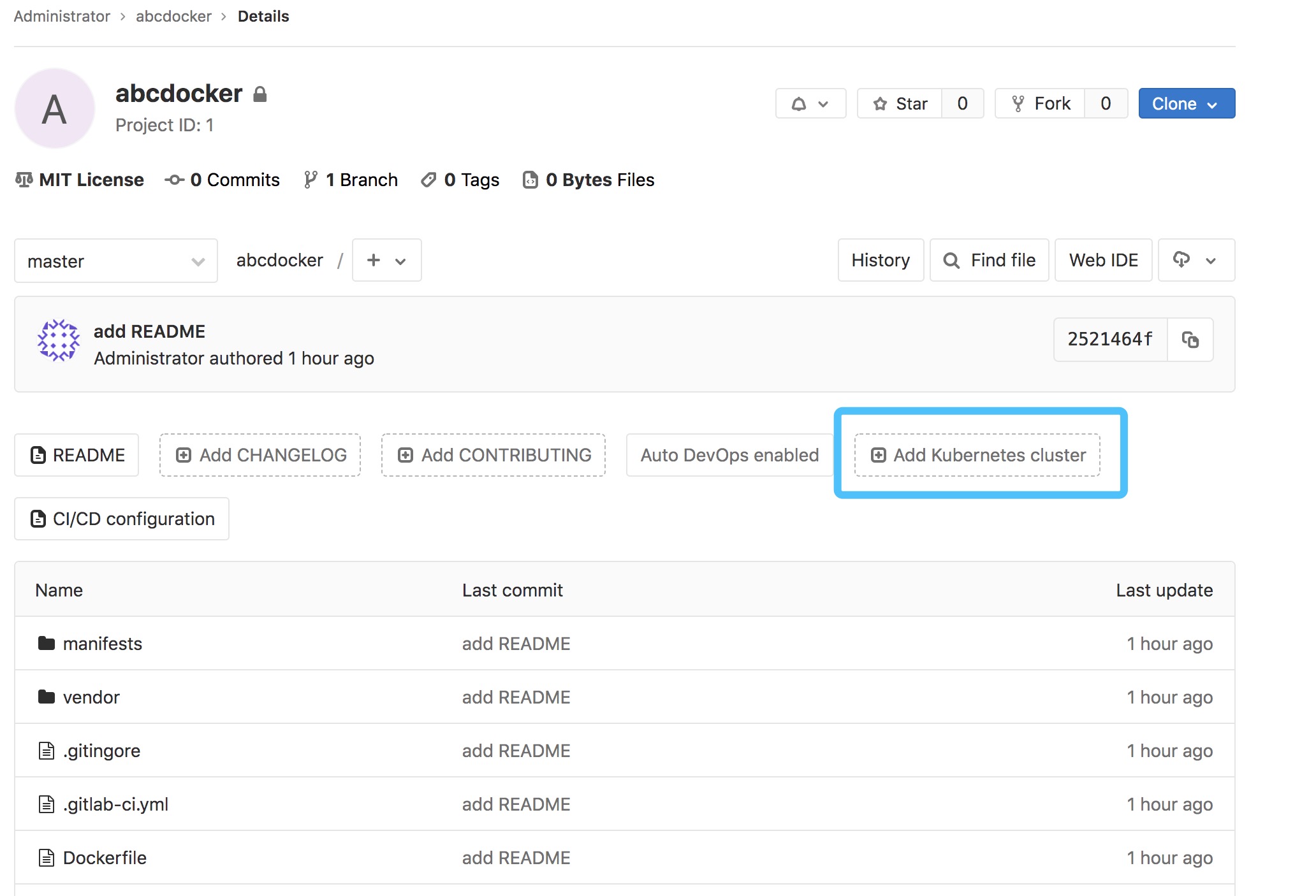
点击添加集群
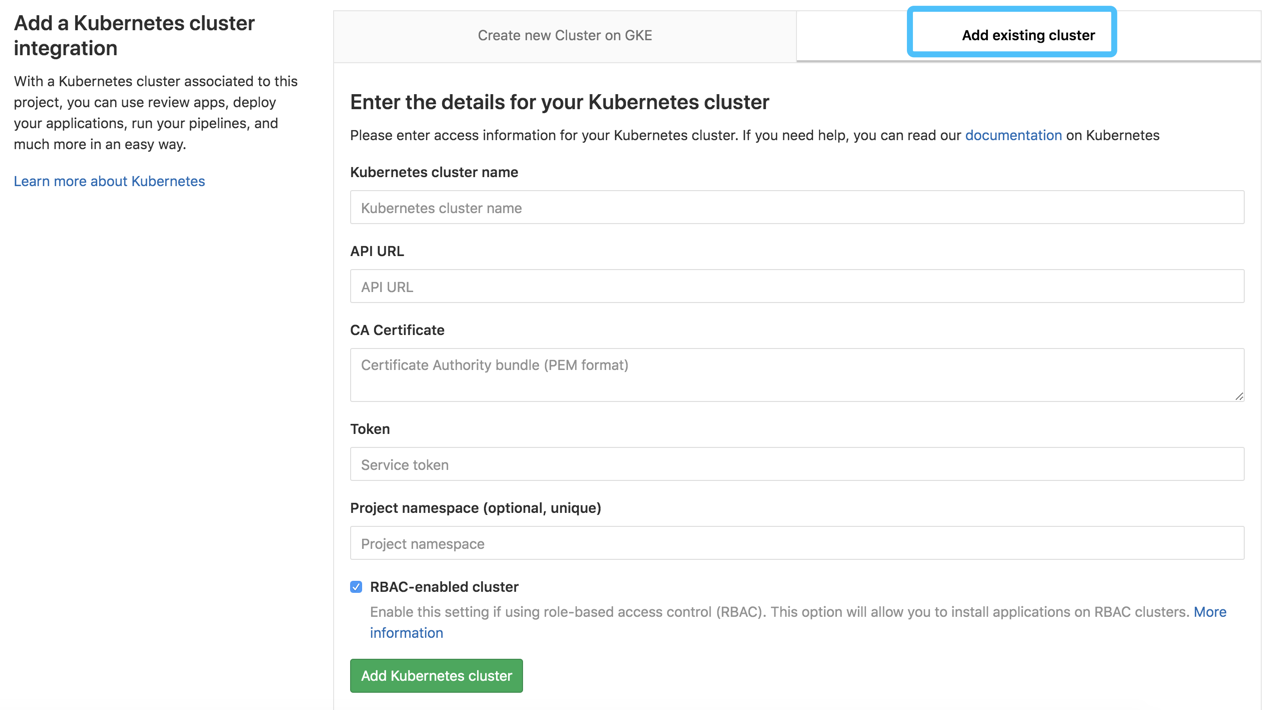
这里简单说一下
Kubernetes cluster name 集群名称能够随便写 API URL 这里实际上就是apiserver地址,经过kubectl cluster-info查看到 CA TOken能够经过/root/.kube/config里面获取到,也可使用下面的方式获取到
获取证书token等相关配置
#除了使用/root/.kube/config获取还能够经过 获取
#这里先建立一个命名空间
kubectl create ns gitlab
#由于在操做的时候会涉及rbac权限的问题,这里要建立一个rbac的文件。咱们将集群的cluster的权限绑定到ServerAccount
[root@yzsjhl82-135 ~]# cat gitlabdemo-sa.yaml
apiVersion: v1
kind: ServiceAccount
metadata:
name: gitlab
namespace: gitlab
---
apiVersion: rbac.authorization.k8s.io/v1beta1
kind: ClusterRoleBinding
metadata:
name: gitlab
subjects:
- kind: ServiceAccount
name: gitlab
namespace: gitlab
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-admin
cluster-admin是内置的一个角色,拥有集群全部权限的一个角色
而后咱们进行建立
[root@abcdocker ~]# kubectl create ns gitlab [root@abcdocker ~]# kubectl apply -f gitlabdemo-sa.yaml serviceaccount/gitlab unchanged clusterrolebinding.rbac.authorization.k8s.io/gitlab created [root@abcdocker ~]# kubectl get sa -n gitlab NAME SECRETS AGE default 1 74m gitlab 1 3m10s
咱们建立的serviceaccount实际上就是一个secret,接下来咱们进行获取token和ca
[root@abcdocker ~]# kubectl get secret -n gitlab
NAME TYPE DATA AGE
default-token-pmlvw kubernetes.io/service-account-token 3 112m
gitlab-token-5cgx2 kubernetes.io/service-account-token 3 40m
[root@abcdocker ~]# kubectl get secrets gitlab-token-5cgx2 -n gitlab -o yaml
apiVersion: v1
data:
ca.crt: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUR4akNDQXE2Z0F3SUJBZ0lVR29Balg2cGdQVUJkL1ZEU2RrbzlvOFR5ckQwd0RRWUpLb1pJaHZjTkFRRUwKQlFBd2FERUxNQWtHQTFVRUJoTUNRMDR4RURBT0JnTlZCQWdUQjBKbGFVcHBibWN4RURBT0JnTlZCQWNUQjBKbAphVXBwYm1jeEREQUtCZ05WQkFvVEEyczRjekVTTUJBR0ExVUVDeE1KTkZCaGNtRmthV2R0TVJNd0VRWURWUVFECkV3cHJkV0psY201bGRHVnpNQ0FYRFRFNU1EZ3lOakV6TURNd01Gb1lEekl4TVRrd09EQXlNVE13TXpBd1dqQm8KTVFzd0NRWURWUVFHRXdKRFRqRVFNQTRHQTFVRUNCTUhRbVZwU21sdVp6RVFNQTRHQTFVRUJ4TUhRbVZwU21sdQpaekVNTUFvR0ExVUVDaE1EYXpoek1SSXdFQVlEVlFRTEV3azBVR0Z5WVdScFoyMHhFekFSQmdOVkJBTVRDbXQxClltVnlibVYwWlhNd2dnRWlNQTBHQ1NxR1NJYjNEUUVCQVFVQUE0SUJEd0F3Z2dFS0FvSUJBUURLNm02UXd2dUwKYWw1S1h2aVFlbDJXL0pFTm5OSVVsalNmUHhraVE2NUloUStLaEVaeEJ3S0hZczNzMFdYMDFVQUtVeDNVVmMxSgo2V3pQL3MvbGlCaC8xVmxwOXpNRFR1OEhjbWdKVW01VnBmTTFhQ1d4eXk2bHZXVWl4V1FadVNCSjFZT2NJN3R4ClZYbktxR3FnS2RuTEJyamJGSWNtdnJFV01RMmRUcjBOWUZuaVd5UkRmQXlpdW11NEtnZEVZSmlIYXFXNm1xYVMKK1d3czFaWEZzRHl6SzNvQWxmTTZ4ZEhXMk9OQ0JadFovaTFtMTBsV3FTS0hsZlBRU1VOcDRMaURHWElaTFpKeApOQ1Z5T2lINFI4T1RaM3dhME9yOVhEeVEzMmIrNkhYa01FMTAvaFc5bnRlanRCZXExVzNjMTVOeVRzemJYYWQzCjJyZ3ZvZ1JtcFNwUkFnTUJBQUdqWmpCa01BNEdBMVVkRHdFQi93UUVBd0lCQmpBU0JnTlZIUk1CQWY4RUNEQUcKQVFIL0FnRUNNQjBHQTFVZERnUVdCQlErQ3RaTWZrbGV1MmtCY0hFc2RzcVMxRVJ5YkRBZkJnTlZIU01FR0RBVwpnQlErQ3RaTWZrbGV1MmtCY0hFc2RzcVMxRVJ5YkRBTkJna3Foa2lHOXcwQkFRc0ZBQU9DQVFFQUF4Wlo5R0NOCmdJMzVWaDNvdE9IUkw4eXJSSEw5b05qbzdVQnZEU2JBZkp2dDd1WGx3WmF0bXBZTUN1MEpVUnJnMWM0Rng3cWUKUHdOQVNnQUFuVHZKZmdEYlZRWDlTM25CcytJYzdTUE5wdXVacTloZzhmSHkyaHRYZ0RiL3lOMkdpNlBBK29zTwpWdWRTYXI5S0tMcVJzNnBuU2tPOEJkbmtPR2llUks5WnJIOVlnS3VodFVhbmZGSEhJeTE0ZXJqQ0s3YUV0S2FOCmxJQVNhV2crYkNnK29JdklqcjdyRzZoU1VFZWkwdVJGbHg5OXN0OVBSeUVaVTZ2MVpETEt6bjY0MUp1elREeDkKTVhLdUtKQUF1anUyc1c0VjZ2VEowR1pGUGNobkxrZSs1NC9QSnVsLytzVExRS1puVE9EMm9KdW1VMEFiVnFMRwpZa1VLUWJ2dUhzMW9sUT09Ci0tLS0tRU5EIENFUlRJRklDQVRFLS0tLS0K
namespace: Z2l0bGFi
token: ZXlKaGJHY2lPaUpTVXpJMU5pSXNJbXRwWkNJNklpSjkuZXlKcGMzTWlPaUpyZFdKbGNtNWxkR1Z6TDNObGNuWnBZMlZoWTJOdmRXNTBJaXdpYTNWaVpYSnVaWFJsY3k1cGJ5OXpaWEoyYVdObFlXTmpiM1Z1ZEM5dVlXMWxjM0JoWTJVaU9pSm5hWFJzWVdJaUxDSnJkV0psY201bGRHVnpMbWx2TDNObGNuWnBZMlZoWTJOdmRXNTBMM05sWTNKbGRDNXVZVzFsSWpvaVoybDBiR0ZpTFhSdmEyVnVMVFZqWjNneUlpd2lhM1ZpWlhKdVpYUmxjeTVwYnk5elpYSjJhV05sWVdOamIzVnVkQzl6WlhKMmFXTmxMV0ZqWTI5MWJuUXVibUZ0WlNJNkltZHBkR3hoWWlJc0ltdDFZbVZ5Ym1WMFpYTXVhVzh2YzJWeWRtbGpaV0ZqWTI5MWJuUXZjMlZ5ZG1salpTMWhZMk52ZFc1MExuVnBaQ0k2SWpFNFptWXlabVpqTFdWak1UVXRNVEZsT1MxaE5UZGxMVFV5TlRRd01HUTNZakk0TkNJc0luTjFZaUk2SW5ONWMzUmxiVHB6WlhKMmFXTmxZV05qYjNWdWREcG5hWFJzWVdJNloybDBiR0ZpSW4wLmxacC02bGdnXzUzcnJiYjI1Y0xQWnlXSlpLQ0JQYUJSc0IybDAzMmNHSEFzSWpLdmJOemVpQnJ4M2U4SGNoVjVxNGJ5NDljem53dmkyeXAzZDJ0TGpZOTZTTUt3UDRQQUJjcFozci1YM2NMUFEzTGZrUkhXZlJyQktNY3BYbm1mRmRnZUJ4LXFTRS00ZFo3LTF3ZzNwTDV1ZkZWaEo1OTlZbHBqXzU4OFpxc0c2YTk4WjR1NDVyeTlpSHd2QV9KRDVDcGRvU1FObDk1ZGw2dDlra0c0NHZET2N1cG5WQkIxS1ByeXJsY3FyMlozVjJ4MEVHQWRxSjdUU0JwZWxSaTIyVmFHcGRyMmdhUjV4dTU4cEVKUjdDYl9BUnBHRVZaZ0JvZF9SWmtWU0FtTkdGVVV2YWZSdHBNZ3RLVTM4RkMzZ1drVVBleVZMY2o4Yk9DQTdscndnUQ==
kind: Secret
metadata:
annotations:
kubernetes.io/service-account.name: gitlab
kubernetes.io/service-account.uid: 18ff2ffc-ec15-11e9-a57e-525400d7b284
creationTimestamp: "2019-10-11T10:51:36Z"
name: gitlab-token-5cgx2
namespace: gitlab
resourceVersion: "6743518"
selfLink: /api/v1/namespaces/gitlab/secrets/gitlab-token-5cgx2
uid: 18f0217c-ec15-11e9-8945-525400a79155
type: kubernetes.io/service-account-token
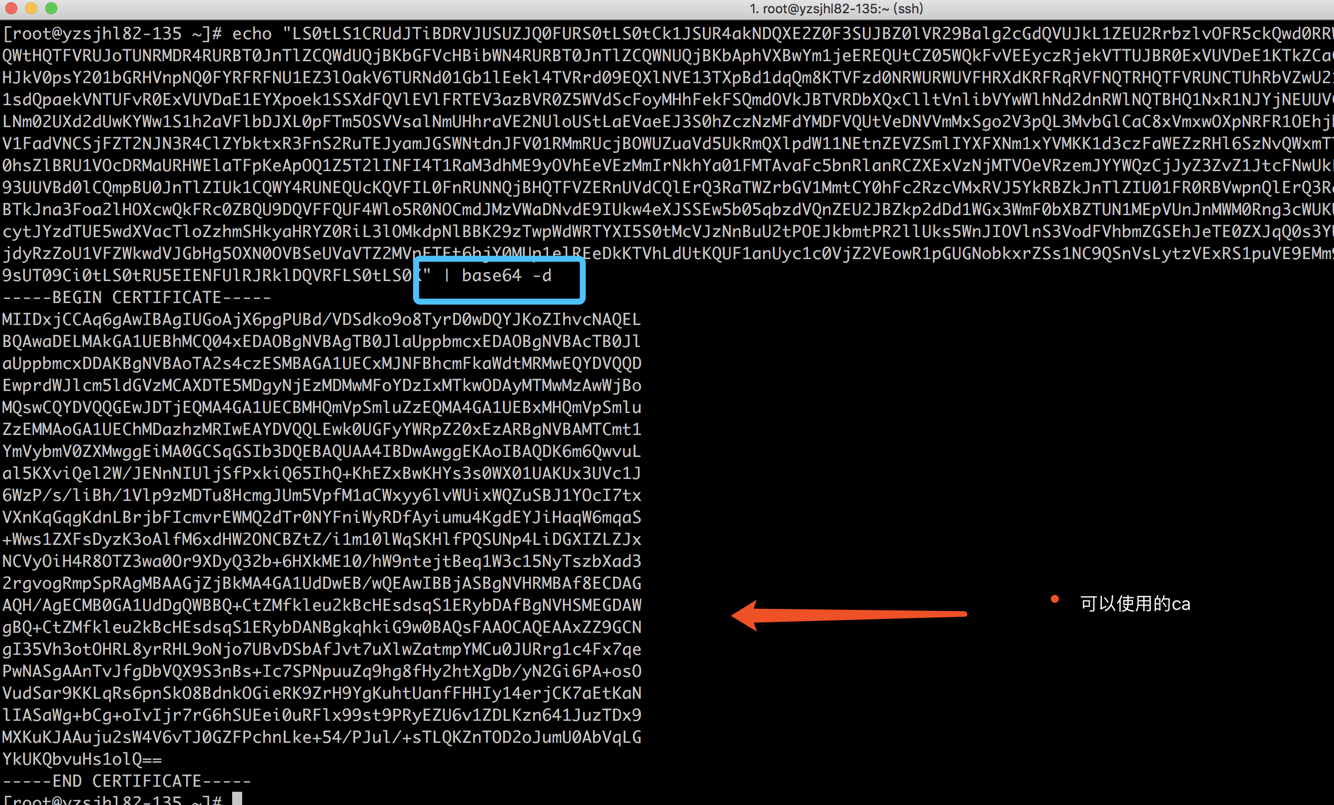
在上面咱们已经看到了ca.crt和token,可是咱们是不可使用。还须要使用base64进行转码
echo "xxxx"|base64 -d #须要复制所有,包括--BEGIN #生成token,方法相同
而后咱们点击ADD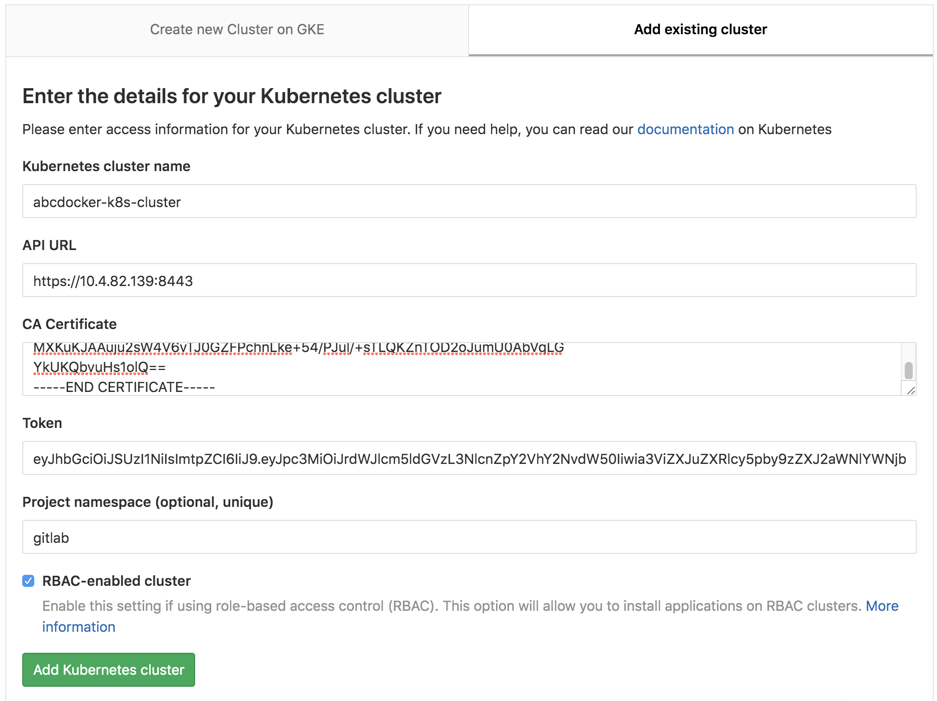
若是咱们点击添加提示下方报错,就须要添加一个容许钩子的一个操做
错误图
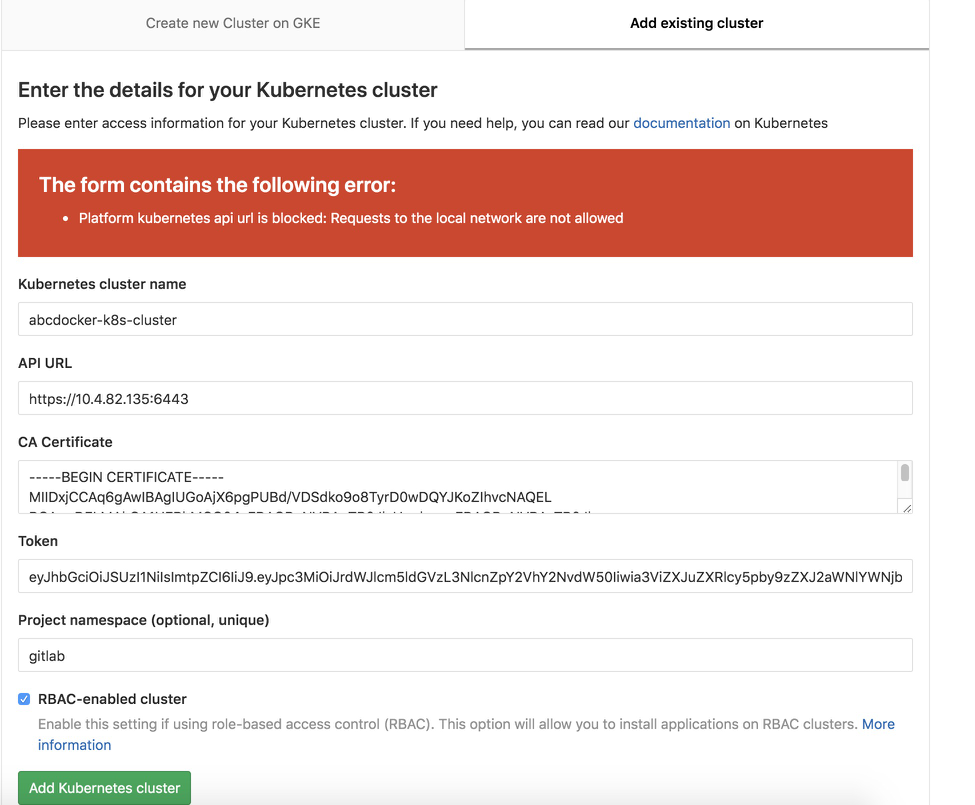
解决方法Admin area => Settings => Network ,而后点击 Outbound requests 右边 的“expand”按钮
添加完成以下图 (如今咱们是已经能够访问到咱们的集群)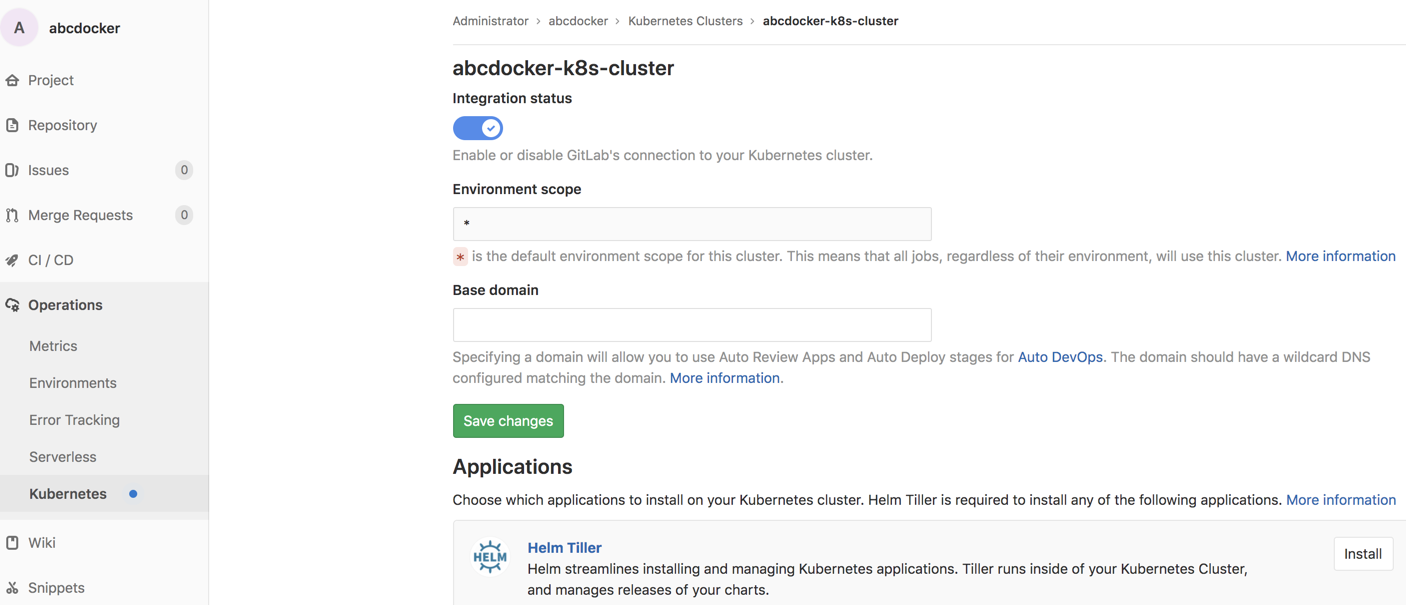
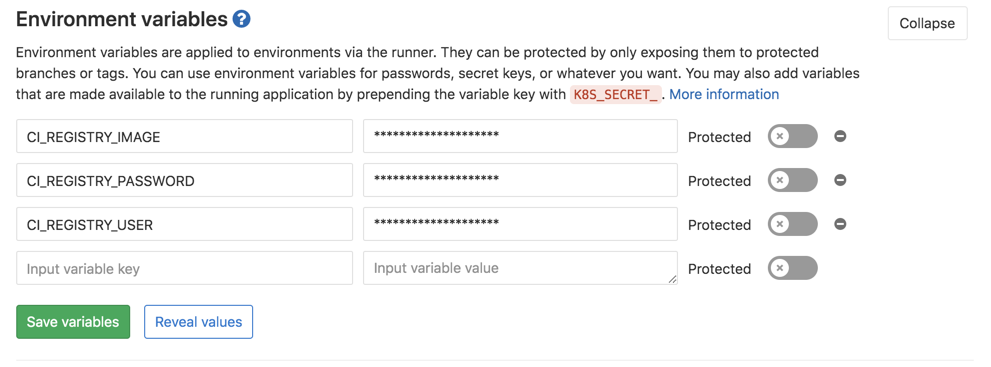
在.gitlab-ci.yaml文件里面,咱们引用了不少环境变量 (好比docker帐号密码文件等)这种文件不能够明文显示,因此在配置文件使用了变量,如今就须要去gitlab上配置一下这个变量
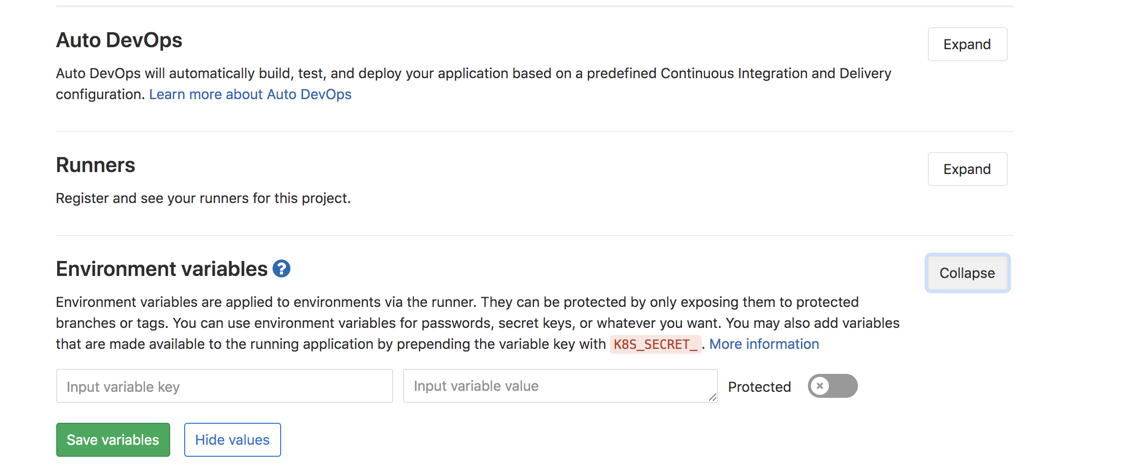
在下面添加镜像地址,容器仓库的帐号密码就能够CI_REGISTRY_USERCI_REGISTRY_PASSWORDCI_REGISTRY_IMAGE
gitlab ci变量文档 https://docs.gitlab.com/ee/ci...
在前面咱们已经提交了git代码,若是没有提交测试能够解压下面的文件,在提交一次
wget http://down.i4t.com/abcdocker-gitlab-demo.tar.gz 代码文件,里面包含gitlab ci脚本及本次演示环境
咱们这里提交一个代码进去,进行演示

在咱们的kube-ops命名空间下,gitlab会生成runner镜像,里面包含咱们ci脚本定义的镜像以及runner镜像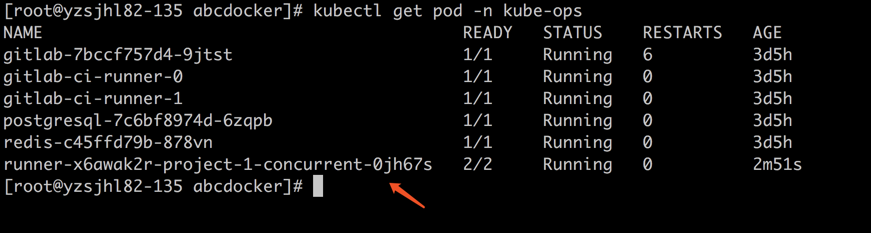
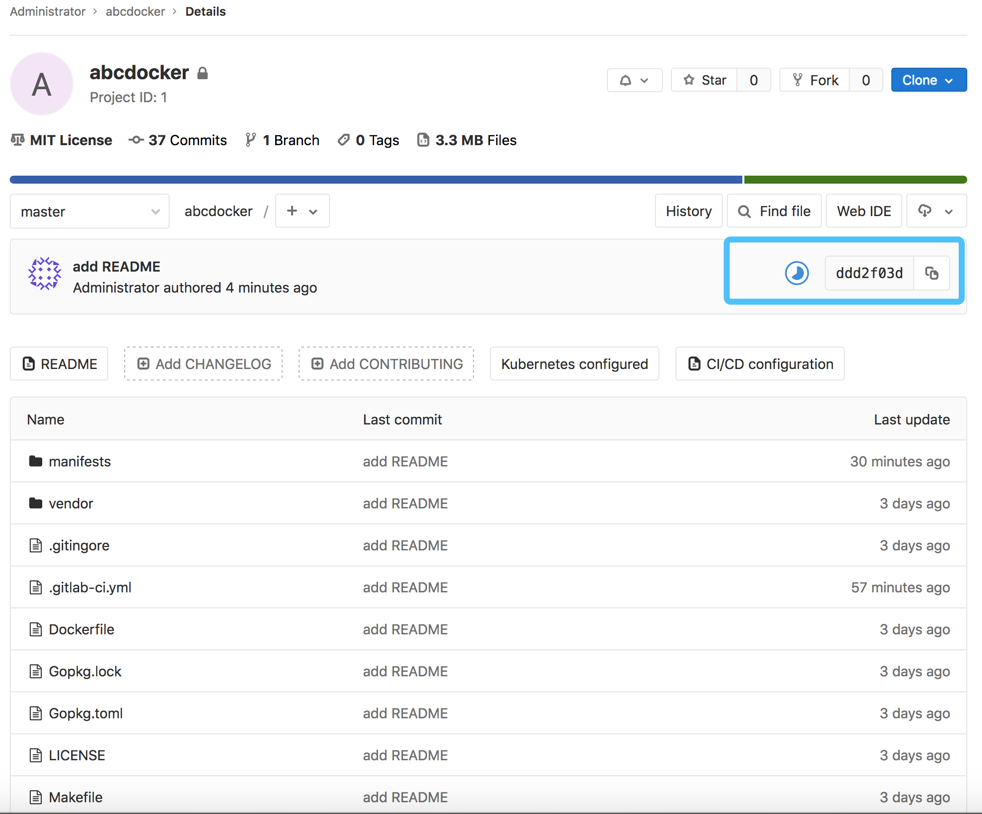
接下来咱们能够在gitlab查看ci构建步骤
构建请注意,若是没有.gitlab-ci.yaml文件,gitlab不会触发ci脚本
点击下方能够看到详细的构建步骤
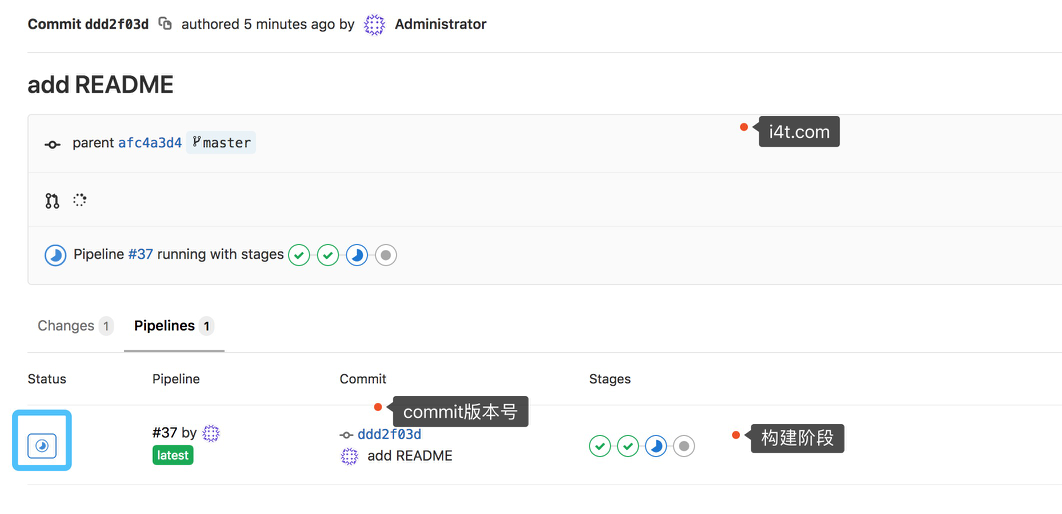
能够查看到详细的构建步骤,和jenkins pipline做用相同
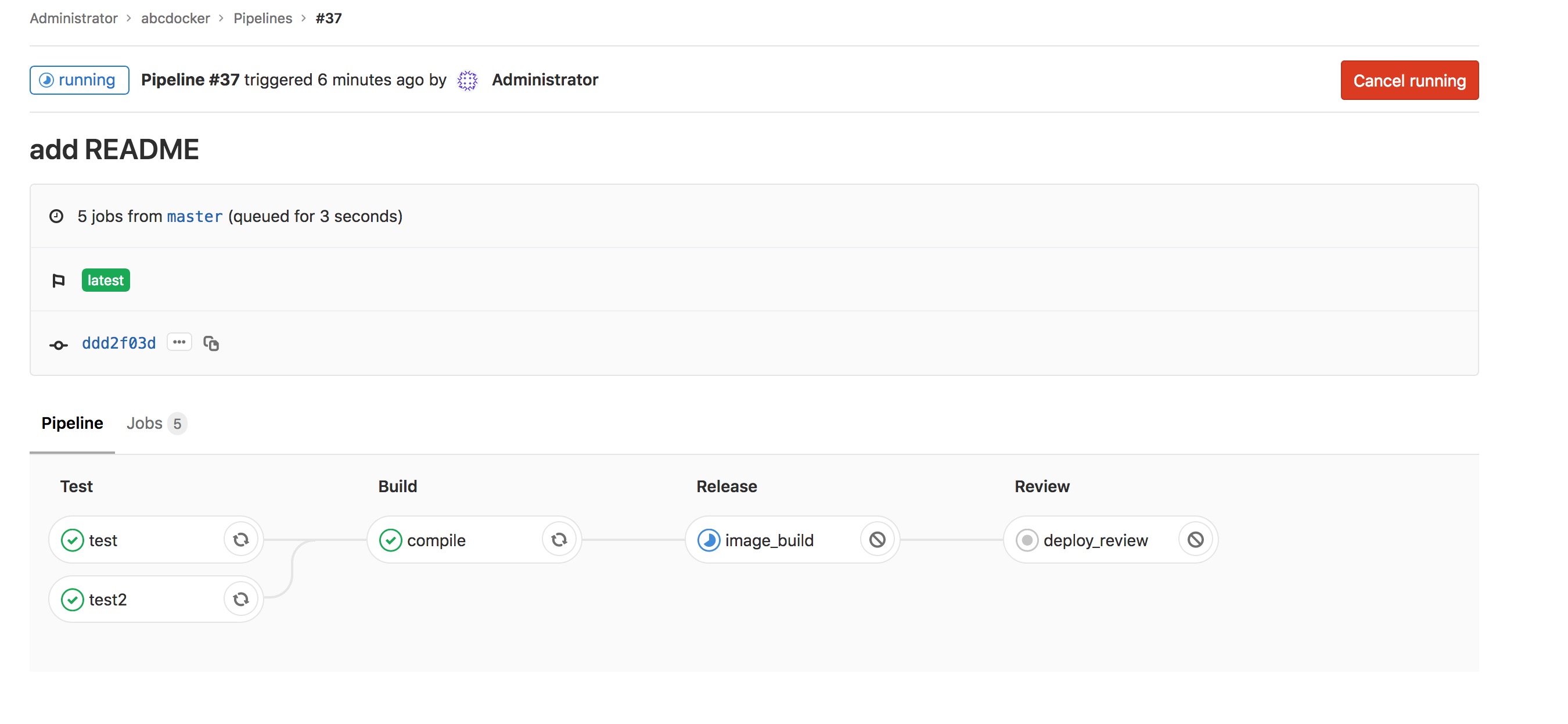
在Build阶段咱们添加了一个变量,使咱们build完成后能够将打包的文件下载下来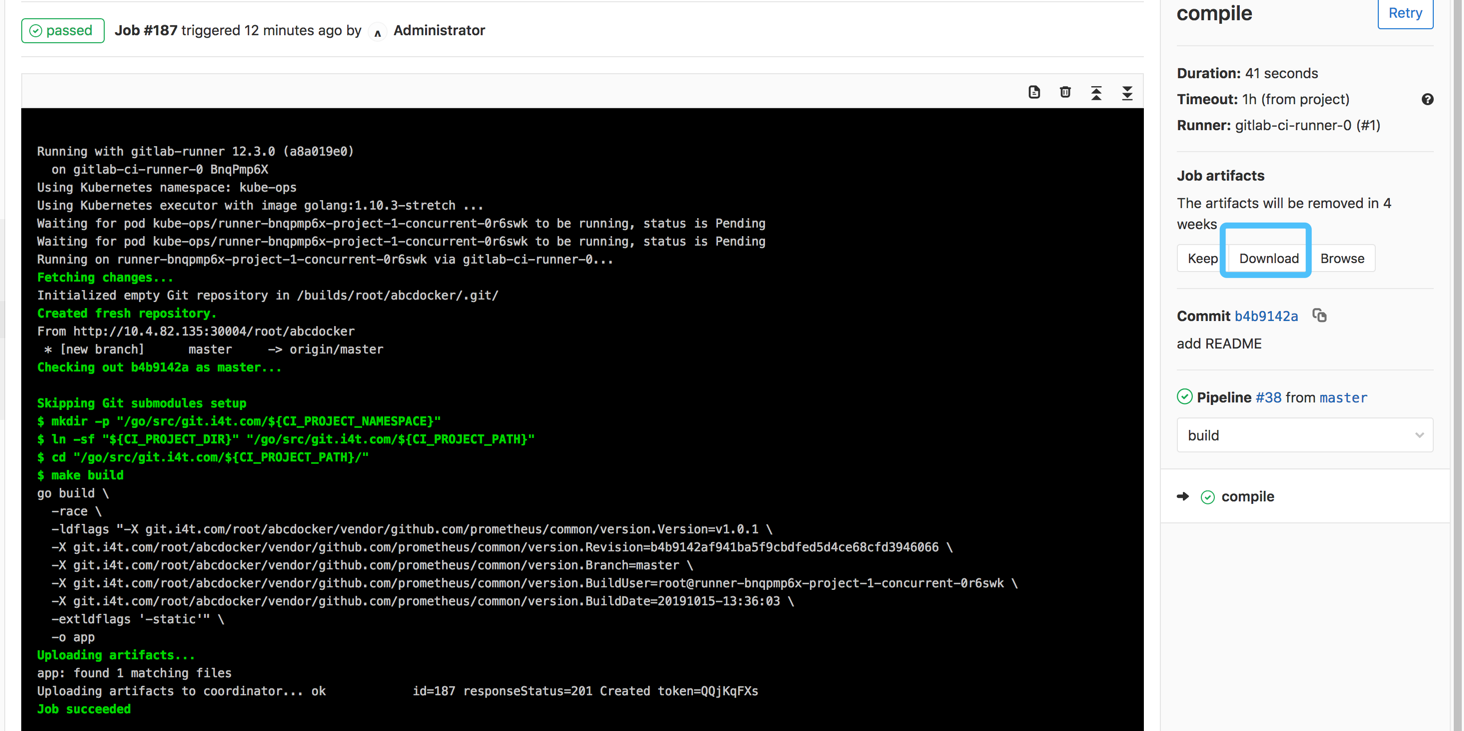
构建完成后就会出现下方,而且还能够重复构建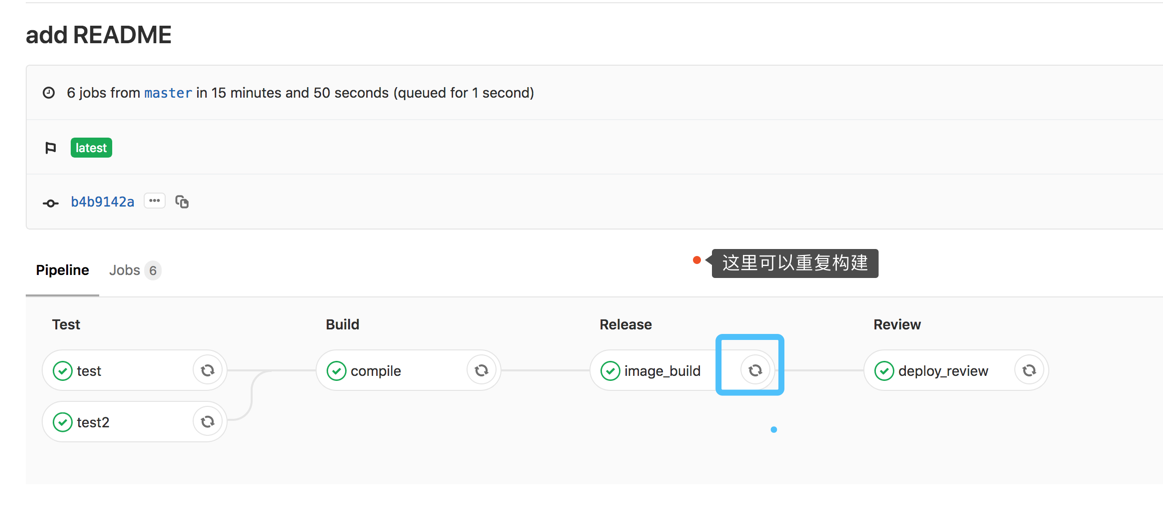
接下来咱们能够查看一下pod和svc等相关状态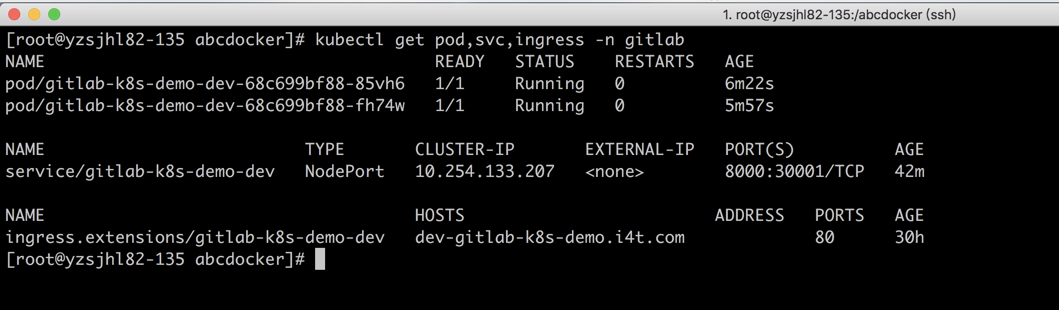
可使用ingress访问,或者经过nodeport方式访问。这里我使用nodeport方式进行访问演示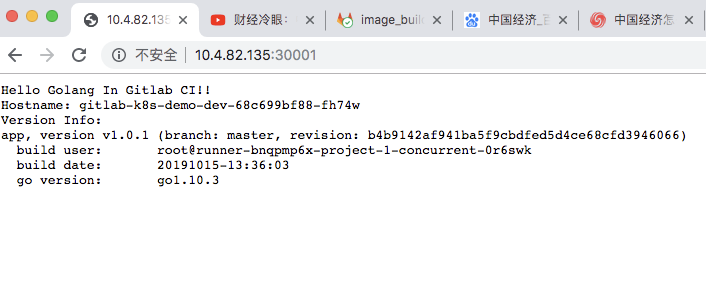
咱们能够根据本身的需求进行修改
小结
1.这里pod的版本号我使用的是commit版本号,能够确保惟一性
2.这里提交代码只有的master上会进行处罚
3.这里个人镜像仓库使用的是阿里云
文档若是有问题请在下方评论,我会及时进行修改并进行答疑。 着急能够点击右下方加群,群里@管理员2019年10月15日21:54:47
- 1. gitlab + gitlab-runner 集成 CICD
- 2. 基于Kubernetes/Jenkins/Harbor/Sonarqube搭建微服务CICD系统
- 3. gitlab 部署 + cicd 集成
- 4. Kubernetes集成Jenkins实现CICD
- 5. DevOps GitLab CICD 实践1——GitLab 部署
- 6. gitlab的CICD搭建记录
- 7. 基于 Gitlab 和 Kubernetes 的 CI/CD 实践
- 8. k8s环境下GitLab+Helm+GitLab Runner Java项目CICD落地实践
- 9. 使用Gitlab Template加强GitLab CICD的扩展性和兼容性
- 10. linux中安装gitlab和cicd(断网版)
- 更多相关文章...
- • Spring基于Annotation装配Bean - Spring教程
- • Spring基于XML装配Bean - Spring教程
- • ☆基于Java Instrument的Agent实现
- • Docker容器实战(八) - 漫谈 Kubernetes 的本质
-
每一个你不满意的现在,都有一个你没有努力的曾经。
- 1. gitlab + gitlab-runner 集成 CICD
- 2. 基于Kubernetes/Jenkins/Harbor/Sonarqube搭建微服务CICD系统
- 3. gitlab 部署 + cicd 集成
- 4. Kubernetes集成Jenkins实现CICD
- 5. DevOps GitLab CICD 实践1——GitLab 部署
- 6. gitlab的CICD搭建记录
- 7. 基于 Gitlab 和 Kubernetes 的 CI/CD 实践
- 8. k8s环境下GitLab+Helm+GitLab Runner Java项目CICD落地实践
- 9. 使用Gitlab Template加强GitLab CICD的扩展性和兼容性
- 10. linux中安装gitlab和cicd(断网版)